i-SOON Operations: A View from Kazakhstan
Leak shows Kazakhstan’s cyber-vulnerability and its importance to China as economic partner and haven for Uyghurs
The massive February 16 2024 leak of materials from Chinese information security company i-SOON showed the company had compromised and stolen data from entities worldwide. The materials included charts with personal data on subscribers of several telecommunications companies in the Central Asian country of Kazakhstan. This oil- and mineral-rich country, formerly part of the Soviet Union and flanked by Russia and China, has pursued a multivector foreign policy, nurturing good relations with a variety of countries. Current president Kassym-Jomart Tokayev, a former diplomat, reportedly speaks fluent Chinese, Russian, French and English, in addition to the Kazakh language (https://online.zakon[.]kz/Document/?doc_id=30100479). His family has discreet business ties to Russia. Kazakhstan is a key transit country for Chinese exports to Europe. The Kazakh ethnic group, culturally Turkic, extends on both sides of the border with China and shares the Muslim religion and cultural similarities with the Uyghur ethnic minority in China’s Xinjiang region. Some Uyghurs fleeing persecution in China have found uneasy refuge in Kazakhstan. All of these features could motivate i-SOON and its government clients to want intelligence on Kazakhstan residents. China has continued to target Kazakhstan in pursuit of its economic and military interests, according to Microsoft reports from 2022 and 2023.
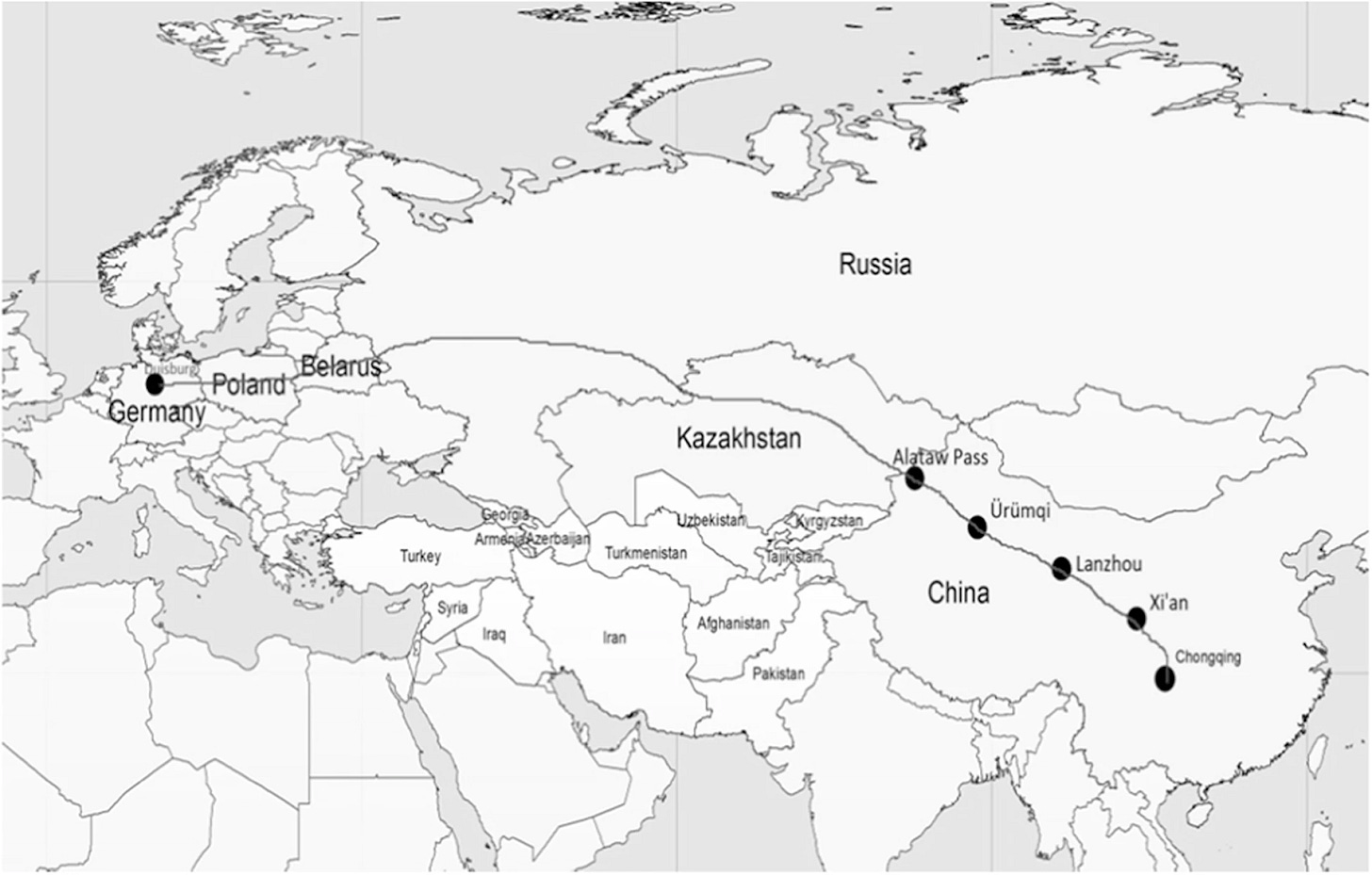
The Trans-Eurasian Railroad (The Chongqing-Duisburg Line). Source: Drawn by Mustafa Ibraheem. From Chen, X., Fazilov, F. “Re-centering Central Asia: China’s ‘New Great Game’ in the old Eurasian Heartland.” Creative Commons Attribution 4.0 International License
Kazakh non-governmental cybersecurity experts critique government efforts
Kazakh telecommunications companies knew hackers were “sitting” in their systems since at least 2021, according to a February 22 article in Russian-language online IT business news source profit[.]kz. The article cites Olzhas Satiyev, the head of Kazakhstan’s Center for Analysis and Research of Cyberattacks (Russian-language acronym ЦАРКА, or TsARKA), a non-governmental association, as saying Kazakh governmental cybersecurity officials likely were aware of the intrusions as well. “And that is only the tip of the iceberg. Nobody knows how many more undiscovered hackers and data leaks there are, Satiyev said.” The leaked files show information about IMEI numbers [mobile phone identification codes], billing data, and call durations relating to customers of communications providers telecom.kz, beeline.kz, kcell.kz, and tele2.kz. Personal data of IDNET and IDTV customers, with usernames and passwords, also appeared in the leak.
A Kazakhtelekom office. By Yaken hgar, 7 June 2007. Source: Wikimedia Commons (https://commons.wikimedia.org/wiki/File:Office_Kazakhtelecom.jpg)
A more detailed report by TsARKA appeared on February 24 on the website of CERT[.]KZ, a non-profit Kazakhstani computer incident response service that is separate from the official government CERT. (The government CERT has the domains cert.gov[.]kz and kz-cert[.]kz). The CERT[.]KZ report provides sample screenshots of Kazakhstan-related data in the i-SOON leak. Items of particular interest include the following:
An entry dated December 2019 for the public website of Kazakhstan’s Pension Fund, on which the i-SOON hackers had noted, “The intranet is completely under [our] control, and user data can be checked for the presence of a name, identifier, address and telephone number….” This suggests that the hackers had access to the Pension Fund as early as 2019. (The Pension Fund denied that its public website includes any personal data of investors or pension recipients).
A screenshot listing selected government agencies of various Asian countries, including an entry mentioning the Kazakh Defense Ministry’s mail server tool.
Screenshots with data of Air Astana, suggesting i-SOON may have had access to data including those who traveled between Kazakhstan and Xinjiang.
TsARKA’s Satiyev said the Chinese state hackers appeared to be particularly interested in employees of what in Russian are called “power agencies” (силовые структуры) – law enforcement, military or intelligence agencies.
TsARKA’s February 24 report posted on the non-governmental CERT[.]KZ website concluded with a critique of the Kazakh government’s cybersecurity efforts. “All this is the result of the haphazard actions and prioritizing of departmental interests over the interest of the state. The structure of a country in which the Information Security Committee is subordinated to the Digitization Ministry will always be vulnerable. Kazakhstan needs a separate, independent agency responsible for cybersecurity – an Agency for Cybersecurity.” Bolstering their assessment of the weakness of Kazakh cybersecurity is a June 2023 SANS Technology Institute report that found Kazakhstan’s main Internet service provider, Kazakhtelecom, appears to rely heavily on outdated and insecure network devices made by a Chinese company Cambridge Industries Group (CIG) and running the vulnerable GoAhead Embedded Web Server. Many of the entities in the i-SOON victim charts were customers of Kazakhtelecom affiliate Almatytelekom.
Official responses avoid naming China
Kazakhstan’s Ministry of Digital Development (full Russian abbreviation МЦРИАП, or MTsRIAP) said it is working with the country’s National Security Committee to analyze the leaked data and to check whether organizations in the country are following rules for data privacy and information security. KZ-CERT [the official one] confirmed that the National Security Committee and its spinoff company “State Technical Service” (Russian acronym АО «ГТС», or AO-GTS) had discovered foreign hacker activity in Kazakh telecoms in 2021. As cited in the February 22 TsARKA report, AO-GTS claimed to have solved the problem, saying, “The measures taken neutralized the threats and risks. The organizers and members of the hacking group have been declared internationally wanted by several countries.” The meaning of AO-GTS’ statement about members’ being on international wanted lists is unclear. Possibly they had in mind the US indictments of hackers associated with Chengdu-404, but did not want to refer to China explicitly. Alternatively, they may have been referring to a separate compromise of Kazakh telecoms by a different hacker group. In either case, their answer seems evasive.
The MTsRIAP ministry acknowledged foreign hacker activity in Kazakh systems but, in contrast to the non-governmental TsARKA and CERT[.]KZ, is in no hurry to point the finger at China’s government. In an article entitled “They Don’t Want an International Scandal?” in Russian-language Kazakhstan-based website bes[.]media, MTsRIAP cybersecurity official Ruslan Abdikalikov tactfully but confusingly said, “We cannot accuse a particular country or special service of violating our laws. That is, we have no direct proof, therefore we want to say that China is a strategic partner of our country. Accordingly, as we understand it, the situation is quite simple: there is a hacker group that definitely worked for some foreign special service.”
Abdikalikov explained that “our operational information security center, which used a Kazakhstan-made tool, discovered the first signs” of hackers’ presence in systems of the company Kcell. Then the National Coordinating Center for Information Security checked and found hacker presence in other ISPs as well. “They spent a year closing off access to hackers.” He added, “If you look at the leak, the freshest information is from 2022. In 2019, 2020, and 2021 they also had some access or tried to obtain access to this infrastructure, and in 2022 we managed to kick them out completely.”
A Cisco Talos report from October 2023 describes an espionage actor it called YoroTrooper, likely associated with Kazakhstan’s government. First active in June 2022, the group focused on defending the Kazakhstan government email system and spying on other former Soviet countries. It also targeted the Kazakhstan government’s own Anti-Corruption Agency, suggesting that it may be helping some faction in domestic political conflicts that often play out in the form of corruption trials. It is possible that the YoroTrooper group may have carried out the kind of defensive actions that MTsRIAP officials claim to have taken against foreign threat actors.
Whatever efforts they took to expel foreign hackers from their systems, these government officials apparently did not deem it important to acknowledge the breach publicly until the i-SOON leak forced their hand.





I wonder if any of the carriers are pure Hauwei. I noticed the Pakistan telco that was also mentioned was specifically a China Mobile operator