Matrix Cup: Cultivating Top Hacking Talent, Keeping Close Hold on Results
Matrix Cup aligns with China’s strategy to enhance its offensive and defensive cyber capabilities by increasing the volume of vulnerabilities available domestically and fostering young hacking talent.
The Natto Team is honored to invite Eugenio Benincasa, a senior researcher at the Center for Security Studies at the Swiss Federal Institute of Technology Zurich (ETH Zurich), to co-author this post. Eugenio’s report “From Vegas to Chengdu: Hacking Contests, Bug Bounties, and China’s Offensive Cyber Ecosystem” is a must-read to understand how China's offensive cyber ecosystem thrives by leveraging civilian hackers who excel in major hacking competitions and bug bounty programs.China’s brand-new hacking contest, Matrix Cup, was inaugurated in May 2024 in Qingdao, Shandong Province, and introduced as a “high-profile and large-scale cybersecurity competition in the Eastern Hemisphere.” This is no exaggeration. Organized by 360 Digital Security Group and Beijing Huayunan Information Technology Co. (also known as VUL.AI), the Matrix Cup brings together China’s highly influential actors from academia and the private sector, featuring various types of challenges and offering substantial monetary rewards. With higher award payouts than any other domestic or international hacking competitions, the Matrix Cup boasts prize amounts of US$ 2.75 million that surpass even Pwn2Own's US$1.1 million (2024) and the Tianfu Cup's US$1.4 million (2023).
Beyond its size and scale, the contest aligns with China’s cyber policies, which emphasize increasing reliance on domestic products as the nation shifts away from US vendors. It prioritizes new talent cultivation and expands the access of intelligence agencies to critical vulnerabilities, as the vulnerabilities found in the contest are likely channeled to the Ministry of State Security (MSS) for potential use in offensive operations.
This analysis first explores the Matrix Cup's structure and its alignment with China’s policy objectives, then examines the contest’s results and targets, and finally, considers how it fits into China’s broader strategic outlook and addresses intelligence needs.

Competition Structure Covers All Categories While Showing Clear Policy Objectives
Hacking competitions typically focus on one main style, such as Capture-the-Flag (CTF) contests, exploit competitions, or artificial intelligence (AI) challenges. CTF contests involve simulated cybersecurity tasks and come in two main types: Jeopardy and Attack-Defense. Jeopardy CTFs resemble digital treasure hunts where teams tackle security puzzles, such as reverse engineering and cryptography, to uncover hidden data (flags) and score points. In Attack-Defense CTFs, teams must defend their own systems while attacking their opponents’ to capture their flags. Unlike CTFs, exploit competitions focus on finding and exploiting vulnerabilities in real systems or software. AI hacking contests, on the other hand, focus on using automated techniques to either defend systems or exploit weaknesses. These often involve creating AI algorithms that can detect and mitigate attacks or develop offensive strategies to outsmart defensive AI systems.
The Matrix Cup features five distinct challenges that combine all three styles of competition, making this China’s first hacking competition to include all three. These include three separate tracks dedicated to vulnerability mining along with one Attack-Defense CTF challenge, and one AI challenge. Payouts are allocated overwhelmingly for vulnerability-related challenges, with 18 million yuan (approximately USD 2.48 million), followed by 1.2 million yuan for the AI challenge (approximately USD 165,000), and 200,000 yuan for the CTF challenge (approximately USD 27,500). The three vulnerability mining contests are divided into:
● General Products Contest (通用产品漏挖赛): While the Matrix Cup's website does not provide an exact target list for this track, it is likely to include Western operating systems, browsers, networking devices, and mobile devices, based on reporting from SecurityWeek, an US-based online security news publication;
● Domestic Software and Hardware Products Contest (国产软硬件安全检测赛): This contest includes Chinese operating systems, switches, routers, and VPNs, though specific targets are not detailed on the contest’s website;
● Original Vulnerability Discovery Contest (原创漏洞挖掘赛): This contest is aimed at college students and focuses on domestic products, according to a write-up by 360 Digital Security.
These tracks operate independently of each other, each with their own rankings and prizes. The emphasis on domestic products is a continuation from the 2023 edition of the Tianfu Cup – a major Chinese exploit contest established in 2018 and held annually in Chengdu – albeit with important differences. From 2018 to 2022, Tianfu Cup participants primarily targeted Western products. Although Chinese products were included in the 2021 edition, the bounties for finding vulnerabilities in them were significantly lower, attracting minimal attention from contestants. The 2023 edition marked a significant shift towards increasing the quantity and prize money for domestic products, though these were all listed together with Western targets instead of being separated into different tracks as in the Matrix Cup.
The increased focus on domestic products aligns with China’s broader policy objective, commonly referred to as “Delete America,” aiming for self-sufficiency in advanced technologies and reducing reliance on foreign suppliers. This highlights the goal of fully domesticating China’s IT infrastructure and replacing foreign-made core components, such as semiconductors, software, and databases, with Chinese-made ones. The introduction of a dedicated track for domestic products at the Matrix Cup has likely added impetus for advancing talent in domestic technology sectors.
Targets and Results Were Kept Internally
Unlike the well-known Tianfu Cup, whose organizers openly displayed the competition targets – particularly including popular foreign products – and the results, the official website of Matrix Cup has not disclosed any competition targets or results of the vulnerability mining challenges. No Chinese media reports mentioned names of any targeted products either. However, SecurityWeek, in a report dated May 13, over a month before the opening of Matrix Cup, did give a list of competition targets. The list included the Windows, Linux and macOS operating systems; Samsung Galaxy, Google Pixel, iPhone and several China-made smartphone brands; enterprise products from Microsoft, Zimbra, F5 and Citrix; networking devices from Cisco, Juniper Networks, SonicWall and Linksys; network-attached storage (NAS) devices from WD, Synology and QNAP; and cybersecurity products from Fortinet, Checkpoint, Cisco, Ivanti (Pulse Secure), and Kaspersky. In addition, targets reportedly also included databases such as MariaDB, SQL Server, MySQL, and Oracle Database; enterprise tools such as Adobe Reader, Microsoft Teams, Zoom and Microsoft Office; the Chrome, Firefox, Edge and Safari web browsers; VMware, QEMU, Docker, Microsoft and Oracle virtualization technologies; an HP multi-functional printer; and the Hadoop data storage and processing framework. SecurityWeek did not state the source of the target list information. The Natto Team could not verify this target list.
A write-up about the Matrix Cup from 360 Digital Security, the host company, gave a summary of the competitions on July 1, 2024, after the competitions were over. It stated that about 100 vulnerabilities were discovered in “internationally renowned software and hardware products including some medium and high-risk vulnerabilities.” During the General Products Contest, which targeted international popular products, 28 medium and high-risk vulnerabilities, covering virtualization platforms, mainstream operating systems, and network devices, were found. The write-up named two winning teams. The TZL team from Tsinghua University won the Best Vulnerability Award by successfully discovering a vulnerability in a virtualization management platform with the highest market share in the world (note from the Natto Team: the platform is likely VMWare). The AAA team from Zhejiang University breached the kernel system of mainstream mobile operating systems (note from the Natto Team: this is likely Apple iOS systems). Gong Guang, the chief judge of the Matrix Cup and the chief security researcher of 360 Digital Security, said the participating teams showed “world-class level” skills, such as “exploiting multiple vulnerabilities in one case and other little-known techniques.”
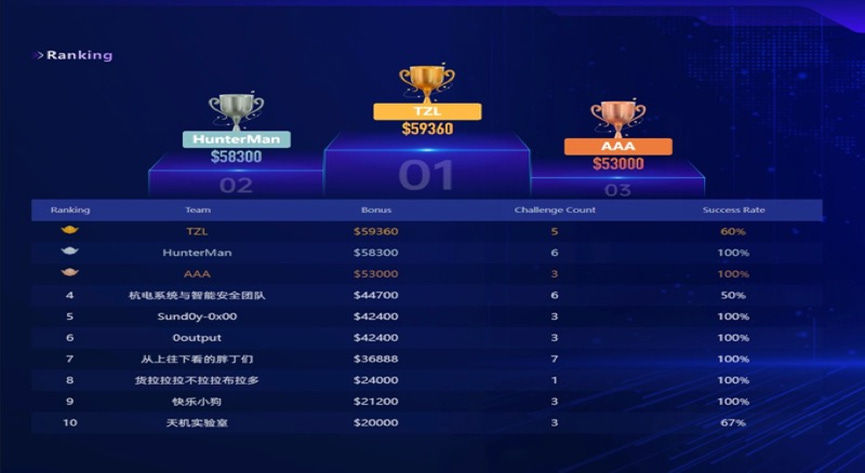
A blog post on Tsinghua University’s website celebrated its students’ results across all five challenges. They achieved first place in the General Products Contest and the CTF Attack-Defense contest, and jointly won the AI challenge with the PLA-affiliated National University of Defense Technology. Notably, the strong participation and performance of university teams in the General Products Contest underscored the absence from the podium of teams from companies well-known for finding critical vulnerabilities at the Tianfu Cup, such as Cyber Kunlun, Ant Group, and Sangfor.
It's unclear how many international participants were involved in each of the five contests. According to 360 Digital Security, the Matrix Cup attracted more than 1,000 teams and nearly 3,000 players from scientific research institutions, government units, and enterprises worldwide, with mentions of foreign teams from Vietnam and Malaysia. The write-up does not detail the extent of international participation in each contest. Traditionally, China-based CTF contests have welcomed international participants, whereas exploit competitions have predominantly featured Chinese participants.
The Importance of Talent Development: Seeking Honkers with Combat Capability
Hacking competitions in China have been known for serving as part of China’s talent pipeline to identify and nurture the country’s “combat talent.” Matrix Cup takes talent development to another level. As Zhou Hongyi, 360 Group founder and the organizing chairman of Matrix Cup, stated in his opening speech: “Matrix Cup places talent development at its core from the very beginning of its design. The competition is not only a technical competition, but also a platform to discover, train and recruit top cybersecurity talent.” In addition, “Matrix Cup is built on the concept of providing real-world scenarios through the simulation of confrontation, penetration, and attack and defense to refine the actual combat ability of [our] cybersecurity talent.” The reason for that, as pointed out by Hu Zhenquan, CEO of 360 Digital Security, is that advanced persistent threat (APT) groups and ransomware groups present a growing threat to China.
The Matrix Cup gathered a large number of Generation Z (people born between the mid-1990s and the mid-2010s) as the main members of the teams, “highlighting the vigorous new force of the cybersecurity industry,” as described by China Information Security Magazine, an official publication of China Information Technology Security Evaluation Center (中国信息安全测评中心), a component of the Ministry of State Security (MSS).
As Zhou pointed out in his opening speech, “the significance of the Matrix Cup is to improve the country’s defensive and offensive cyber capability.” This emphasis also showed itself in his choice of words to refer to the competition participants. He called them “red hat hackers” (“红帽子黑客”). Red hat hackers, in the Chinese context, are understood to refer to the early generation of patriotic hackers from the 1990s who called themselves “honkers” (“hong-ke” is a transliteration of the Chinese word 红客, which means “red hackers”). (For more on this early generation of patriotic hackers, see the chapter “Becoming a Cyber Superpower: China Builds Offensive Capability with Military, Government and Private Sector Forces” in the book “The Emergence of China’s Smart State.”) Zhou’s use of the red hat hackers term in the current context likely intended to revive the younger generation’s patriotic spirit. Indeed, 360 Digital Security CEO Hu said that having China’s own hacking competition is critical to cultivate “capable combat-ready honkers.”
The patriotic spirit of the early honkers was also highlighted by the participation of the so-called Honker Community (红客社区) as one of the three co-organizers of Matrix Cup (The other two co-organizers were Yongxin ZhiCheng (永信至诚, Integrity Technology) and Saining Network Security (赛宁网安, CyberPeace)) . The Honker Community, an online hacking community platform, is likely affiliated with 360 Digital Security. In a speech at the 7th Digital China Summit in May 2024, 360 Digital Security vice CEO Bu Sinan discussed how the company nurtures “new quality talents” and mentioned the creation of the “Honker Community to gather experts and white hat technical talents from various cities, enterprises and universities.”
Having China’s Own Hacking Competition is Strategically Important
Since at least 2018, China has discouraged its security researchers from competing in foreign exploit competitions, such as Pwn2Own. The organizing chairman of Matrix Cup and founder of 360 Group Zhou Hongyi was the key player pushing for that change. Zhou stressed the importance of having China’s own hacking competitions again at the Matrix Cup. When China has its own hacking competitions, “the results can stay in China and be used by the country to defend cyber security, since globally vulnerability has been considered as a strategic military technology.” The reason for not participating in overseas hacking competitions, particularly competitions hosted in North America, was because “we may expose 0-day vulnerabilities we have and exploits we have developed” … “It is not worthwhile for us to expose our hacking techniques and the value of vulnerability for the amount of cash rewards,” Zhou said at the Matrix Cup opening speech. On the other hand, continuous discovery of vulnerabilities is as important as keeping vulnerabilities in China.
The vulnerabilities discovered during the Matrix Cup are likely channeled to the Ministry of State Security (MSS) for evaluation for cyber operations: Chinese law mandates that researchers must report newly found vulnerabilities to state authorities within 48 hours of discovery, and China’s hacking competitions have been linked to state-sponsored operations in the past. The inaugural edition of the Tianfu Cup in 2018 raised suspicions that an exploit revealed during the competition was used by the Chinese government to conduct espionage operations against the country’s Uyghur minority population. In 2024, the i-Soon leaks further substantiated these suspicions, as outlined in Winnona DeSombre’s analysis for Margin Research. Leaked internal chat logs indicated that exploits from the Tianfu Cup 2021 were transmitted to the "public security bureau" (MPS) in Jiangsu – likely referring to the MSS instead (refer to the CSS Cyberdefense report “From Vegas to Chengdu” for a comprehensive outlook on the contest).
Additionally, the contest's organizers are well-known for their close ties to the government and for supplying newly discovered vulnerabilities to the MSS. In 2023, Dakota Cary and Kristin Del Rosso detailed a vulnerability-sharing framework between private companies and China’s National Vulnerability Database of Information Security (CNNVD), overseen by the MSS. Private companies are categorized into three tiers based on their annual vulnerability submissions to the CNNVD, with Tier 1 requiring the highest number of reports. The competition’s main organizers, 360 Digital Security Group and VUL.AI, are Tier 1 CNNVD members, whereas the co-organizers, Saining Network Security (also known as CyberPeace) and Yongxin Zhicheng (also known as Integrity Technology Group), are Tier 2 members, respectively.
What’s Next?
The Matrix Cup adds to China’s growing ecosystem of exploit competitions, providing another opportunity for Chinese security researchers to compete and win at home in China, since they are no longer encouraged to attend Western competitions. In the short term, this increases the volume of vulnerabilities available to China’s security agencies and keeps top talent motivated by loosening the participation bottleneck in these competitions, which often have a limited number of available spots. In the long term, the Matrix Cup’s emphasis on talent development and vulnerability discovery, both within domestic and international products, aligns with China’s strategy for enhancing its offensive and defensive cyber capabilities.





