Salt Typhoon: the Other Shoe Has Dropped, but Consternation Continues
Sichuan Juxinhe, directly involved in the Salt Typhoon cyber operations, resembles a front company of the Chinese Ministry of State Security
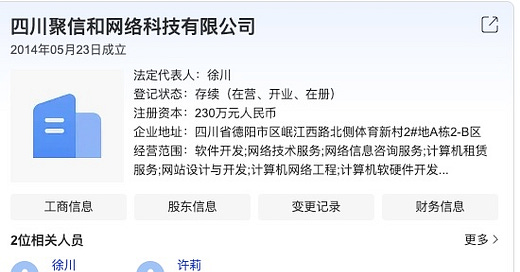
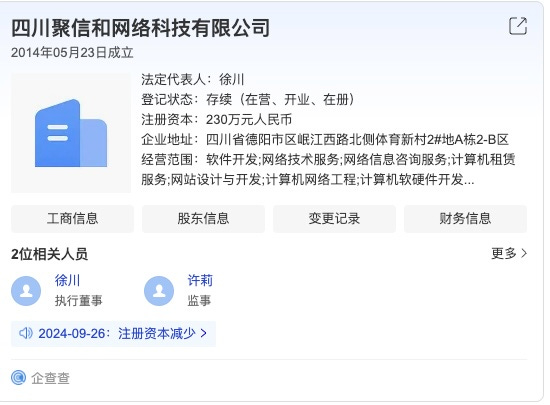
On January 17, 2025, the United States government imposed sanctions on Sichuan Juxinhe Network Technology Co., LTD (Sichuan Juxinhe) (四川聚信和网络科技有限公司)., a Sichuan-based cybersecurity company, accusing it of “direct involvement in the Salt Typhoon cyber group,” a China-linked cyber threat group. Salt Typhoon, active since at least 2019, has compromised the network infrastructure of multiple major US telecommunication and internet service provider companies. Many in the industry have been expecting attribution and intrusion details for months after the Wall Street Journal first exposed Salt Typhoon in September 2024. Now the question is how Sichuan Juxinhe was involved in the exploitation of these US telecommunication and internet service providers. However, without intrusion details and with sparse publicly available information about the company, It is not easy to pinpoint the connections. Nevertheless, the Natto Team’s preliminary research discovered that Sichuan Juxinhe is likely a front company of China’s Ministry of State Security (MSS).
What does an MSS Front Company Look Like?
The January 17 press release from the US Department of Treasury about Sichuan Juxinhe’s sanctions stated that the Chinese Ministry of State Security (MSS) “has maintained strong ties with multiple computer network exploitation companies, including Sichuan Juxinhe.” When a Chinese cybersecurity company has ties with the MSS, the company often can be categorized into two types: a real business working for the MSS through contracts or a front company set up and operated by the MSS or MSS proxies, as the Natto Team has previously shown in the report “Front Company or Real Business in China’s Cyber Operations.” A front company may appear to be a legitimate business, but its goal is not to make profits but rather to pursue a hidden agenda: to conduct cyber operations to serve the Chinese state’s objectives.
Over the years, researchers’ reports and US Department of Justice (DoJ) indictments have identified quite a few front companies that the MSS established as disguises for its cyber operations. For example, the following front companies are allegedly associated with Chinese Advanced Persistent Threat (APT) groups APT10, APT40 and APT31, respectively:
Tianjin Huaying Haitai Science and Technology Development Company ( 天津华盈海泰科技发展有限公司) (Tianjin Huaying Haitai), established in 2010, was allegedly associated with APT10, a threat group operated by the MSS’s Tianjin State Security Bureau.
Hainan Xiandun Technology Development Co., Ltd. (海南仙盾科技开发有限公司)(Hainan Xiandun), established in 2011, was allegedly associated with APT40, a threat group operated by the MSS ‘s Hainan State Security Department, a provincial state security bureau.
Wuhan Xiaoruizhi Science and Technology Company (武汉晓睿智科技有限公司) (Wuhan XRZ), established in 2010, was allegedly associated with APT31, a threat group operated by the MSS’s Hubei State Security Department.
Besides their alleged direct association with the MSS, these front companies share several common characteristics that the Natto Team has identified through examining reports and DoJ indictments:
they have a limited digital footprint.
they are registered to provide information technology services but do not show much business activity.
they have fewer than 10 employees.
their entries in business registries show no records of legal or operating risks.
they often have registered no intellectual property in patent or copyright databases.
Does Sichuan Juxinhe Fit the Mold of a MSS Front Company? It Has Almost All the Characteristics Plus One More
Available company information on Sichuan Juxinhe shows that it has almost all the front company characteristics that we identified above.
Sichuan Juxinhe, established on May 23, 2014, is in business operation as of this writing. The company’s executive director is Xu Chuan (徐川) and director Xu Li (许莉). (Though both transliterated as "Xu," the two last names differ in the Chinese original). Sichuan Juxinhe is located in Deyang, Sichuan Province. Deyang is a second-tier city1 around 40 miles northeast of Chengdu, the capital city of the province. Its proximity to Chengdu, a hacking hub, likely provides convenient access to talent and tooling resources for cyber operations. Its location outside Chengdu might have been intentional to avoid attention.
However, perhaps because of its growing “business” needs, the Natto Team discovered that Sichuan Juxinhe established a subsidiary company in Chengdu itself in July 2021. The subsidiary, Sichuan Juxinhe Network Technology Company Chengdu High-Tech Branch ( 四川聚信和网络科技有限公司成都高新分公司), is located in Chengdu’s high-tech district.
The Natto Team research on Sichuan Juxinhe across several Chinese search engines yielded little information. This indicates that Sichuan Juxinhe has a limited digital footprint, with no media reporting about the company or its business activities. Several Chinese business registration databases showed identical business information for the company. As to the number of the employees, Sichuan Juxinhe is registered as having only two of them. Business registries show no records of legal or operating risks. All features match the characteristics of a front company, as we discussed previously.
In addition, Natto Team research also discovered that Sichuan Juxinhe has another name: Deyang Qianai Cultural Communication Co. (Deyang Qianai) (德阳千爱文化传播有限公司). It appears that the company originally registered using the name Deyang Qianai in 2014 then changed its name to Sichuan Juxinhe in the same year. The term “Cultural Communication Co.” applies to Chinese companies in a variety of sectors such as consulting and administration, commercial services, or digital marketing. “Qian Ai” is unrevealing, literally meaning “thousand love.” The change of the company’s name from the town name, Deyan, to the province name, Sichuan, suggests it was expanding its importance in the business world. Although the reason for changing the company’s registered name is unknown, the two names of the company make it look like two completely different businesses. This adds another layer of suspicion that this may be a front company.
Sichuan Juxinhe’s Area of Focus, Communication System Services, Aligns with Salt Typhoon Targeting
The company’s registered scope of business lists a variety of information technology services it provides, including:
software development;
network technology services;
network information consulting services;
computer leasing services;
web design and development;
computer network engineering;
computer hardware development, design and sales;
installation, debugging, maintenance of telecommunication system equipment, as well as
the development of hardware and software for telecommunication systems.
Sichuan Juxinhe’s expertise in telecommunication systems aligns with the company’s alleged role in Salt Typhoon activity targeting the network infrastructure of numerous major US telecommunication and internet service provider companies.
Surprisingly Sichuan Juxinhe Owns a Number of Software Copyrights. Why is It?
The last characteristic of a front company that the Natto Team identified previously was that a front company often has registered no intellectual property in patent or copyright databases. However, surprisingly Sichuan Juxinhe owns a number of software copyrights. One database of company information states that Sichuan Juxinhe owns 15 software copyrights, most of which are for software related to network routers and network switches. Six examples of copyrighted software which the Natto Team identified were all registered in 2021, including:
network router information detection software (likely network monitoring software)
network router document management software
network router wireless access software
network switch call ticketing analysis system
network switch backend support system management software
network switch configuration software
Sichuan Juxinhe seemed to work hard and devoted its nominally two-man operation to developing software related to network routers and network switches. Although little public information on Salt Typhoon’s tactics is available, investigators looking at the Salt Typhoon activity initially suspected the threat actors may have obtained access to Cisco routers; earlier in 2024, reports had emerged of Chinese abuse of Cisco routers. Although we need intrusion details to determine the applications, Sichuan Juxinhe definitely has been developing the relevant capability to target these companies.
Despite that, owning software copyrights does not align with characteristics of a front company that we have known before. It makes us wonder why Sichuan Juxinhe, which otherwise acts like a MSS front company, registered 15 software copyrights. Is it possible that Sichuan Juxinhe registered these copyrights on behalf of a division of the MSS as a source of income for the division, so that whoever uses this software needs to pay? The Natto Team has no definitive answers.
Now we know Sichuan Juxinhe was directly involved in the Salt Typhoon operations after more than three months of Salt Typhoon news hype. The other shoe has finally dropped, but we still need more intrusion details to defend against the threats. We are afraid that personnel reshuffling in the new US administration could slow ongoing investigations and any release of new technical details.
For details of China’s city-tier classification, see this China Briefing article.