Beyond the Aliases: Decoding Chinese Threat Group Attribution and the Human Factor
Examining the overlap between APT27, HAFNIUM, and Silk Typhoon through recent U.S. government disclosures, and why understanding the humans behind the keyboard is important for cyber defenders
Since March 2025, the U.S. government has exposed Chinese hackers and entities linked to threat groups publicly tracked as APT27, HAFNIUM, Silk Typhoon, and other threat group monikers. Among these named Advanced Persistent Threat (APT) groups, technical analysis and observed intrusion activities from the cybersecurity community have provided group tracking criteria and measures to mitigate harm and to eradicate malware from systems and networks. Because cybersecurity firms often use different threat models, have their own standards for clustering intrusions, and closely guard their telemetry data—often not sharing with others—we see threat groups labeled with a number of “a.k.a.” (also known as) group names. For example, the profile of APT27 on Malpedia, a community-curated online malware encyclopedia and resource, lists 16 a.k.a. group names. How do these a.k.a. groups overlap? How are they different from one another? The answers are not always clear.
Additionally, when law enforcement and government agencies disclose the real identities of people and organizations behind or linked to threat groups, especially the connections between these entities and the groups, it adds another layer of complication. For instance, in a March 2025 alert about the indictments of Chinese hackers Yin Kecheng and Zhou Shuai, issued by the U.S. Federal Bureau of Investigation (FBI), it states that “Yin and Zhou’s activities are publicly tracked as APT27, Threat Group 3390, Bronze Union, Emissary Panda, Lucky Mouse, Iron Tiger, UTA0178, UNC5221, and Silk Typhoon.” How should we interpret this statement? Does this mean that APT27 and the other threat group names mentioned are equivalent a.k.a. groups? Or were Yin and Zhou involved in the operations behind all of these groups?
In this post, the Natto Team examines threat groups named APT27, HAFNIUM, and Silk Typhoon—which, in many reports, appear as “a.k.a.” names for each other—to demonstrate how the cybersecurity community tracks threat groups and the nuances involved in choosing which group name to highlight when government documents disclose identified individuals and entities.
We will also shed light on the importance of the human factor in the cyber ecosystem. The people behind the keyboard, and their motivations, culture and relationships, have been a prime focus of Natto Thoughts since its launch in April 2023.
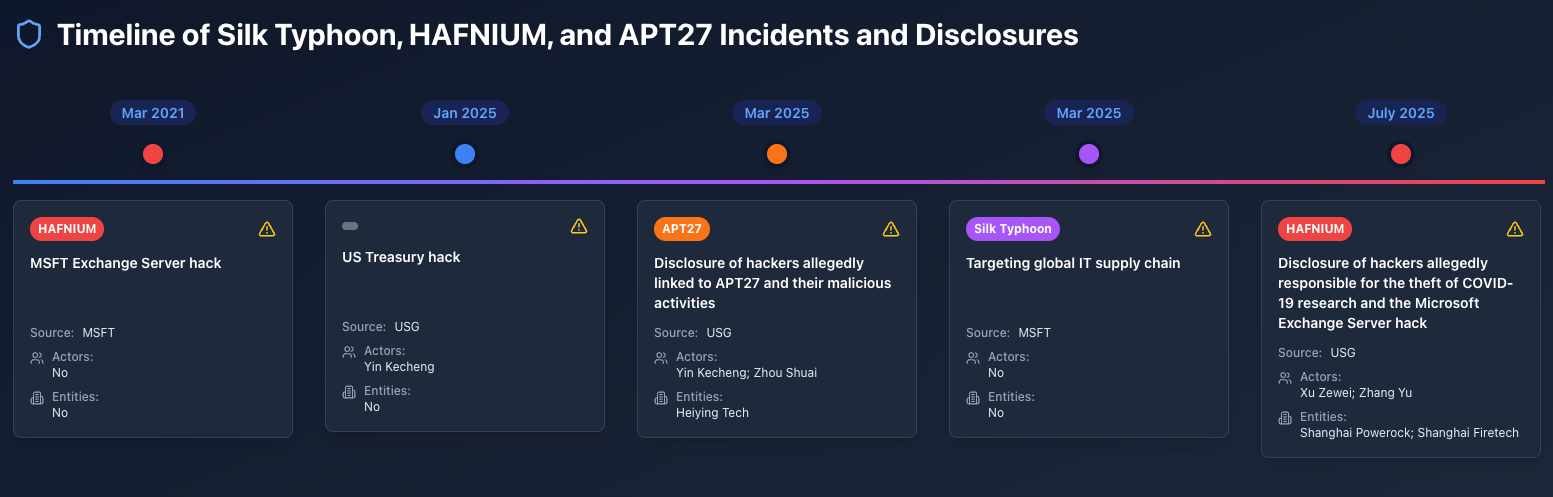
March 2021: HAFNIUM = Silk Typhoon - Microsoft Exchange Server Data Breach
Among the three threat group names, we can clearly equate the HAFNIUM group with the Silk Typhoon group. Both names originated from Microsoft’s threat actor naming taxonomy. In April 2023, Microsoft changed its taxonomy from a system based on chemical elements to a weather-themed system, resulting in HAFNIUM being renamed Silk Typhoon.
The public first learned about HAFNIUM in March 2021, when Microsoft attributed to that group the compromise of Microsoft Exchange Server in that year. In its March 2021 report, “HAFNIUM targeting Exchange Servers with 0-day exploits,” Microsoft assessed HAFNIUM as a “state-sponsored” group “operating out of China.” HAFNIUM has targeted infectious disease researchers, law firms, higher education institutions, defense contractors, policy think tanks, and NGOs in the U.S. The observed TTPs (tactics, techniques, and procedures) included:
Exploiting vulnerabilities in internet-facing servers
Using legitimate open-source frameworks for command and control
Exfiltrating data to file-sharing sites after gaining access
Although the HAFNIUM group name was new to the public at the time, cybersecurity researchers had already reported other overlapping threat groups primarily linked to the use of the China Chopper malware since at least 2013. Malpedia’s HAFNIUM profile cites over 90 reference reports over time.
January 2025: Hacker Yin Kecheng Revealed, but No Threat Group Affiliation Mentioned
On January 17, 2025, the U.S. Department of the Treasury sanctioned Chinese hacker Yin Kecheng, citing his involvement in the Treasury hack that occurred in December 2024. The press release stated that Yin “is affiliated” with the Chinese Ministry of State Security (MSS) and has been active for over a decade. However, it did not mention Yin’s connection to any known APT groups.
March 2025: Yin Kecheng, Zhou Shuai and the APT27 Network
Two months later, on March 5, 2025, the U.S. Department of Justice (DoJ) unsealed two separate indictments alleging that Chinese hackers Yin Kecheng (尹可成) and Zhou Shuai (周帅) (also known as “Coldface”) carried out a hacking campaign targeting a wide range of U.S.-based victims—including the Department of the Treasury—from 2011 to the present. The indictments also revealed that these two hackers are linked to “APT27” and other threat group names, including “Silk Typhoon.” However, the DoJ emphasized the hackers’ connection to “APT27” in the press release headline, noting that both Yin and Zhou operated as freelancers, acting as data brokers who have “sold illegally exfiltrated data and access to compromised computer networks” since at least 2018. Their known TTPs for the identified intrusion activities include:
Routinely scanning victim networks for vulnerabilities, exploiting those vulnerabilities, and conducting reconnaissance once inside the victim’s network
Installing malware to maintain persistent access and communicating with malicious external servers and other hacking infrastructure
Identifying and stealing data
Selling the stolen data
Notably, historical data shows that intrusion activities linked to APT27 can be traced back as far as 2009. Malpedia’s APT27 profile lists over 380 reporting references since 2009 and identifies 11 malware families.
Alongside the two indictments, the U.S. Department of the Treasury added Zhou Shuai and his company, Shanghai Heiying Information Technology Company (上海黑英信息技术有限公司), to the sanctions list, for allegedly “illegally acquiring, brokering, and selling data from highly sensitive U.S. critical infrastructure networks,” in collaboration with sanctioned hacker Yin. Natto Thoughts has published a detailed report about Zhou Shuai, his affiliated companies, and their involvement in Chinese state cyber operations.
March 2025: Silk Typhoon Targeting Global IT Supply Chain
On the same day that the U.S. DoJ identified these two alleged APT27 hackers, Microsoft published a report titled “Silk Typhoon Targeting IT Supply Chain,” outlining observed Silk Typhoon threat activities since late 2024. This marked Microsoft’s first public report about Silk Typhoon (formerly known as HAFNIUM) after renaming HAFNIUM to Silk Typhoon in April 2023.
The report noted that Silk Typhoon has targeted “information technology (IT) services and infrastructure, remote monitoring and management (RMM) companies, managed service providers (MSPs) and affiliates, healthcare, legal services, higher education, defense, government, non-governmental organizations (NGOs), energy, and others located in the United States and throughout the world.” Aside from IT supply chain targets, all other sectors targeted were similar to those identified in Microsoft’s 2021 report on HAFNIUM. The report profiled Silk Typhoon as:
An espionage-focused Chinese state actor
A well-resourced and technically proficient group capable of rapidly operationalizing exploits for newly discovered zero-day vulnerabilities in edge devices
Possessing one of the largest targeting footprints among Chinese threat actors
Demonstrating expertise in understanding cloud environments
Cybersecurity analysts have noted that this activity represents “a significant shift in tactics” by Silk Typhoon due to the group’s increased focus on the IT supply chain.
Although Microsoft did not mention specific victims of Silk Typhoon’s IT supply chain attacks in its March report, an advisory from the U.S. Cybersecurity and Infrastructure Security Agency (CISA), issued on May 22, 2025, warned of cyber threat activity targeting Commvault’s SaaS (Software as a Service) cloud application. Commvault is a U.S.-based data security and cloud infrastructure management company. Following the CISA advisory, various media outlets reported that the Commvault campaign was conducted by the Silk Typhoon group—the same group that “infiltrated Treasury Department networks.”
July 2025: “HAFNIUM” Intrusion Campaign Attributed to Hackers Xu Zewei and Zhang Yu, Along with Their Affiliated Companies
The arrest of the alleged Chinese state-contracted hacker Xu Zewei (徐泽伟) in Italy in July 2025 prompted the disclosure of hackers and companies allegedly associated with HAFNIUM’s threat activities during 2020 and 2021. On July 8, the U.S. Department of Justice issued a press release and unsealed an indictment, accusing Xu Zewei and his co-defendant Zhang Yu (张宇) of participating in hacking activities between February 2020 and June 2021. These activities were reportedly linked to the APT group HAFNIUM and involved the theft of COVID-19 research from universities, the exploitation of Microsoft Exchange Server vulnerabilities, and the compromise of thousands of computers worldwide, including in the United States.
The targeted sectors—“healthcare, law firms, higher education, defense contractors, policy think tanks, and non-governmental organizations (NGOs)”—described in the indictment are similar to those in Microsoft’s 2021 Exchange Servers breach report. The tactics, techniques, and procedures (TTPs) are also identical, including:
Reconnaissance and data gathering by searching open websites for leaked data about targeted infrastructure
Using tools like China Chopper and exploiting zero-day vulnerabilities
The indictment of Xu and Zhang also revealed two companies—Shanghai Powerock Network Company (上海势岩网络科技发展有限公司) and Shanghai Firetech Information Science and Technology Company (上海势炎信息科技有限公司)—in which Xu and Zhang held positions, respectively. These companies operated “at the direction of” the Shanghai State Security Bureau (SSSB), a local office of the Ministry of State Security (MSS).
Natto Thoughts has published a detailed report about Xu Zewei, his affiliated company Shanghai Powerock, and China’s cyber ecosystem. Dakota Cary from SentinelLabs also wrote an excellent report about hacker Zhang Yu, Shanghai Firetech, and China’s covert cyber capabilities.
Which Threat Group Name Should Be Used Among All the Alias Names in Official Documents? It Depends
As the above timeline shows, when the U.S. government discloses alleged hackers and entities responsible for malicious cyber activities—and their links to threat groups tracked by the cybersecurity community—it does not consistently use a single threat group name among all the alias names.
Three government documents from 2025 provide an example: First, in January, the government identified the hacker Yin Kecheng as responsible for the U.S. Treasury hack but did not associate Yin with any specific threat group. Then, in March, the Department of Justice unsealed two indictments against Yin Kecheng and Zhou Shuai separately, while the Treasury Department sanctioned Zhou and his company, Shanghai Heiying; the official documents linked these actors to APT27. Lastly, in July, after the arrest of hacker Xu Zewei, the DOJ unsealed an indictment against Xu Zewei and Zhang Yu and their affiliated companies. This time, the official documents linked the actors to HAFNIUM. HAFNIUM was a Microsoft threat group name, but Microsoft replaced it with Silk Typhoon two years ago. The most likely reason the official documents used the group name HAFNIUM is that the attributed malicious activities—in this case, the compromise of Microsoft Exchange Server and targeting U.S.-based COVID-19 research universities and institutions—were attributed to the HAFNIUM group in 2021. If this reasoning is valid, the APT27 case follows a similar logic: the malicious activities conducted by Yin and Zhou were linked to APT27 activities tracked by the cybersecurity community. Therefore, the official documents chose to use the group name APT27, rather than other alias group names.
Attribution Gaps When Threat Groups Are Not Equivalent to Identified Persons and Entities
In an ideal scenario, we would hope that the cybersecurity community could use a unified threat group naming taxonomy, eliminating naming confusion. Official government documents would not have to pick and choose which threat group name to use when disclosing affiliated real-world persons and entities. However, in reality, many cybersecurity firms have their own threat group or actor naming taxonomies.
Recently, we have seen collaborative efforts among firms to “bring clarity to threat actor naming.” For example, in June 2025, Microsoft and CrowdStrike announced that they have been working to align their threat actor taxonomies. Google/Mandiant and Palo Alto Networks’ Unit 42 have also contributed to this initiative. We hope these efforts will minimize naming confusion in the future and create greater transparency in threat group tracking.
When it comes to identifying real individuals and entities linked to threat groups, another level of confusion arises. Using the example of Silk Typhoon, HAFNIUM, and APT27: if these three group names have been observed with overlapping threat activity clusters, the question becomes what the relationship is among the four identified people—Yin, Zhou, Xu, and Zhang—and three affiliated companies. The indictments state that Yin and Zhou worked together to broker stolen data, and Xu and Zhang appeared to have a work relationship as well. However, it is not clear how the four individuals and affiliated companies are connected or how the US government identified them as part of an overlapping threat activity cluster. The Natto Team has explored the range of companies associated with APT activity, ranging from front companies to jack-of-all-trades infosec companies competing for government contracts.1
Despite the complexity of real identities and threat activity clusters, the Natto Team believes it is important to understand the humans of the cyber ecosystem.
Timo Steffens, a threat intelligence analyst at the German Federal Office for Information Security (BSI), states in his book “Attribution of Advanced Persistent Threats” that “the most advanced level of attribution is the identification of specific organizations and individuals.” Over the past decade, U.S. government agencies have disclosed the identities of numerous persons and organizations allegedly linked to various cyber threat activities through indictments, sanction documents, cybersecurity alerts and advisories, domain seizure records, and unsealed search affidavits and complaints. The Natto Team has compared the insights to be gained from U.S. federal indictments and from leaks. This information is valuable for understanding the humans behind the keyboard—not only their tradecraft but also their motivations, intents, self-image, habits, grievances, weak spots and human foibles, and even the teahouse culture of hacker hotspots such as Chengdu2—and for bridging the gap between government cyber actions and tactical threat intelligence.
Evidently, the human aspect of threat attribution introduces additional complexity into the threat landscape. However, recognizing the connections between individuals, organizations, and their cyber activities is essential for developing a comprehensive understanding of malicious operations.
See, for example, the Natto Thoughts reports linked above, as well as Natto Thoughts reports on i-SOON (here, here and here) and on Sichuan Silence Information Technology; Salt Typhoon; Flax Typhoon-Linked Company Integrity Technology; Business Priorities of Chinese Cyber Range Providers; Sichuan Silence Information Technology; and the Pangu team and other vulnerability researchers.
See, for example, Natto Thoughts profiles of hackers such as Guan Tianfeng of Sichuan Silence and patriotic-hackers-turned-businessmen Zhou Shuai of APT27 and Jiang Jintao a.k.a. “Cold Flame.”


Fascinating deep dive into the human layer of threat attribution. The observation about how U.S. government documents selectively use different threat group names (APT27 vs HAFNIUM) based on the specific malicious activities being attributed is illuminating - it reveals that these are operational clusters, not monolithic organizations. What's particularly valueable is your examination of the relationships between the identified hackers (Yin, Zhou, Xu, Zhang) and their affiliated companies operating as MSS contractors. The point about the collaborative efforts between Microsoft, CrowdStrike, and Unit 42 to align taxonomies is important, but I wonder if the underlying problem is that threat grouping itself is fundamentally a problem of clustering observed behavior, not mapping organizational reality. The teahouse culture insights in Chengdu provide crucial context that technical IOCs alone can't capture.